
2018
Operation Soft Cell Cyberattack
CoreGuard protects critical infrastructure from corruption or highjacking
Telecommunications companies are a prime target for cyberattackers. Whether it’s a private group infecting systems with ransomware in the hopes of monetary gain or state-backed organizations attempting to spy on adversaries, telcos have incredible amounts of valuable private data that attackers are all too eager to access.
The rollout of 5G only makes this data more vulnerable. The software-based infrastructure is inherently vulnerable, and the devices that will connect to the network will provide potentially billions of different entry points attackers can use to gain access to the broader network and execute a widespread attack.
The precedent for such an attack has already been set, well before 5G ever became a reality. In 2018, a pervasive cyberattack was discovered in the networks of major telecommunication providers, including organizations such as T-Mobile, AT&T, and Vodafone. This attack, called “Operation Soft Cell” is believed to be active since at least 2017 but could have been executed as early as 2012.
Operation Soft Cell is considered to be an espionage-motivated attack, backed by the Chinese government. That’s because the bad actors used a unique set of tools that are often associated with the Chinese government-backed group, APT10.
This multi-wave attack spanned at least six years and over the course of that time the group was able to obtain over 100GB of call record data on over 200 million entities, including call and messaging logs, device information, and tower location data which could provide the physical location of the phone and its owner. This data, while not providing information on the content of calls and messages being sent, could provide a detailed picture of a person’s movements and personal network.
To gain initial access to the network, the attackers used a code injection attack by exploiting a vulnerability in poorly written code within the network infrastructure. Once executed, the attackers had complete control over the network. They used this access to steal private data over a number of years, however, it could have been used to do even worse—they could have shut down service altogether if they wanted to.
Attack Overview

Target
Telcos around the world

Aim
Exfiltrate 100GB of call record data
Vector
Code Injection

Result
7 years of stealing data—could have shut cell networks down

Goal
Highly targeted intelligence gathering on key individuals
Attackers Gained Access Via One Corrupted Device
The first indicator that an attack was underway was when a malicious web shell was identified on an IIS web server. From that web shell, APT10 was able to execute various reconnaissance commands, steal credentials, and obtain information about everything from the compromised server to the network architecture.
With the necessary credentials now in hand, the hacking group was able to move across the network to compromise other points of critical infrastructure, including gaining total control over the domain server. With multiple machines compromised and code injected to multiple points across the network, the attackers were able to steal data unconstrained for up to six years, until they were finally discovered.
Operation Soft Cell is notable for a few reasons. First, the attack shines a light on the extreme vulnerability of critical network infrastructure. It’s absolutely imperative that servers, controllers, and other devices that operate within this environment be secured. With a 5G rollout, this need is compounded—5G is projected to support the connectivity of billions of devices. If attackers are able to gain access to the network, as they did in the Operation Soft Cell attack, the private data on those billions of devices could easily be compromised.
The pervasive nature of Operation Soft Cell also brings to the forefront the need for real-time cyberattack detection. Remember, APT10 had years to accomplish their goal before they were discovered. Had an attack detection solution been in place that was able to catch the attack in real-time, the damage could have been not just mitigated but prevented entirely.
Had CoreGuard® been protecting the web server that was initially targeted, Operation Soft Cell would have been stopped before any serious damage was done.

”What really worries me is the amount of access they have—the complete access they have to the network. The worst thing they can do is sabotage it and one day just shut down the whole network.”
— Amit Serper Principal Security Researcher, Cybereason
 Stopping Code Injection Attacks with CoreGuard
Stopping Code Injection Attacks with CoreGuard
In this case, where code injection was the primary threat vector, CoreGuard’s Read-Write-Execute (RWX) micropolicy would have stopped this attack from the beginning, never allowing access or any data to be stolen.
The RWX micropolicy is included in CoreGuard’s base set of micropolicies and it protects against all code injection attacks. RWX does this by providing fine-grained access control, protecting memory reads, writes, and execution.
The RWX micropolicy labels each word in memory with metadata that indicates whether it is readable, writable, and/or executable. Then it blocks any attacks that try to manipulate data in a way that it shouldn’t be. For example, if a software vulnerability like the common buffer overflow is exploited, and then an attacker injects code to write data in a region of memory labeled as readable, the RWX micropolicy blocks that instruction from occurring, and CoreGuard issues a violation.
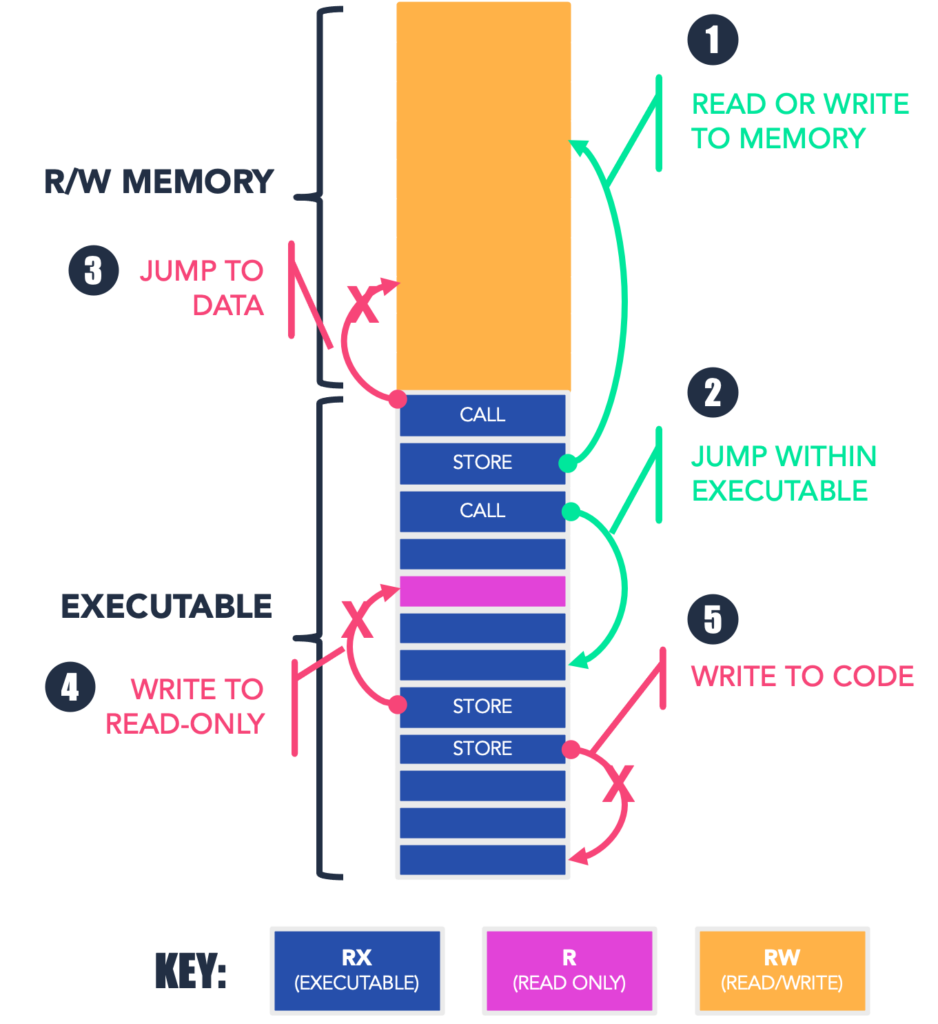
Using the diagram above, let’s look at a couple more examples of how the RWX micropolicy works. The diagram shows memory used by an application, with the top (orange) region being read/write memory and the bottom being a mix of executable instructions (blue) and static, read-only data (pink). The green arrows represent normal, allowed behavior, including:
-
- a store to Read-Write memory, and
- a call from one instruction to another.
These are actions that CoreGuard could have allowed to go through.
The red arrows indicate instructions that would be blocked by CoreGuard’s RWX micropolicy:
-
- a jump into the read/write area (which might be an attacker attempting to execute injected code),
- an attempt to write (store) into read-only memory, and
- an attempt to overwrite code.
So, in the case of Operation Soft Cell, CoreGuard’s RWX micropolicy would have blocked the attacker’s attempt to write code to a part of memory that was not writeable, thus shutting the door to the network and not granting them access.
The pervasive nature of Operation Soft Cell enabled the group behind the attack to be active for years before it was eventually discovered and stopped. Although the attackers didn’t try to take down the network, they did successfully steal 100GB of private call record data on over 200 million entities. Operation Soft Cell proved that a pervasive, years-long attack can infect and compromise multiple providers across entire networks and highlights the fact that critical infrastructure needs to be secured.
The rollout of 5G only heightens the threat of attacks. The expansive connectivity of the network without the necessary security of its critical infrastructure is a recipe for disaster. CoreGuard provides the security and real-time attack detection these networks need in order to be safe.
To learn more about CoreGuard and how it protects critical infrastructure against cyberattack, request a demo today.
Request A DemoOur Solutions
Read-Write-Execute (RWX)
Function: Establishes traditional Read/Write/Execute permissions for code and data, but with a fine-grained resolution
Type of Attacks: Stops code injection attacks


