
2014
German Steel Mill Cyberattack
CoreGuard ensures the safe and proper functioning for safety-critical systems
The Danger of Cyber-Physical Attacks
In 2014, an unnamed German Steel Mill suffered a sophisticated cyberattack that targeted the industrial control systems of a blast furnace, causing the furnace to shut down improperly. This unstable and improper shutdown caused “massive damage” to the furnace and garnered the attention of cybersecurity experts around the world. This was only the second known cyberattack to cause physical damage to its intended target, preceded by the Stuxnet malware of 2009.
Although neither the attacker nor their motives have been confirmed, there has been a lot of speculation, ranging from cyber-sabotage at the hands of the steel mill’s competitors to an attack executed by a government intelligence agency, due to its similarity to Stuxnet and the Triton malware attack of 2017. Whether or not a consensus will be drawn as to who was responsible, analyses of the attack have been able to provide insight into how the attack was executed and, as a result, how similar attacks like this can be prevented in the future.
Attack Overview
Target
Steel Manufacturing Facility in Germany
Aim
Gain Access to the Plant Network via Industrial Operators

Attack Vector
Spear Phishing Emails

Result
Shut Down a Blast Furnace Improperly
Goal
Cause Massive Physical Damage & Result in Potential Loss of Life
How the Cyberattack was Executed
The malware that infected the steel mill was delivered through a series of spear-phishing emails. The attackers specifically targeted industrial operators with the goal of gaining access to the plant network. From there, they were able to exploit previously unknown software vulnerabilities in the industrial control systems, take over the system, and cause multiple components to fail. Most notably, they were able to bypass the standard shutdown procedure of an industrial blast furnace.
This was particularly problematic because, once a blast furnace is blown in and the production of hot metal starts, it typically runs for 10-20 years before being shut down for relining. In order to shut down a furnace safely, a very specific process must be followed. In the case of the German Steel Mill, attackers forced the furnace into an unregulated shut down which resulted in massive physical damage.
Luckily, no injuries were sustained by any of the employees working in the mill. However, a similar improper shutdown of a blast furnace in the UK resulted in an explosion that killed two and injured thirteen others. While this tragedy was caused by human error, the German Steel Mill attack proves that a bad actor, potentially thousands of miles away, can force industrial control systems into deadly scenarios. Preventing cyber-physical attacks from occurring needs to be a top priority as future attacks pose a real risk not just to the equipment but also to human safety.

”Failures accumulated in individual control components or entire systems … As a result, the plant was unable to shut down the blast furnace in a regulated manner … which resulted in massive damage to the system”
— Bundesamt für Sicherheit in der Informationstechnik
 Preventing The German Steel Mill Cyberttack With CoreGuard
Preventing The German Steel Mill Cyberttack With CoreGuard
As previously mentioned, the shutdown process for a blast furnace is a very strict, step-by-step process that must be followed in sequential order—it’s a perfect example of a finite state machine.
At a high level, let’s say the shut down steps are as follows:
- Schedule Shutdown
- Confirm Shutdown
- Blow Down Furnace
- Complete Shutdown
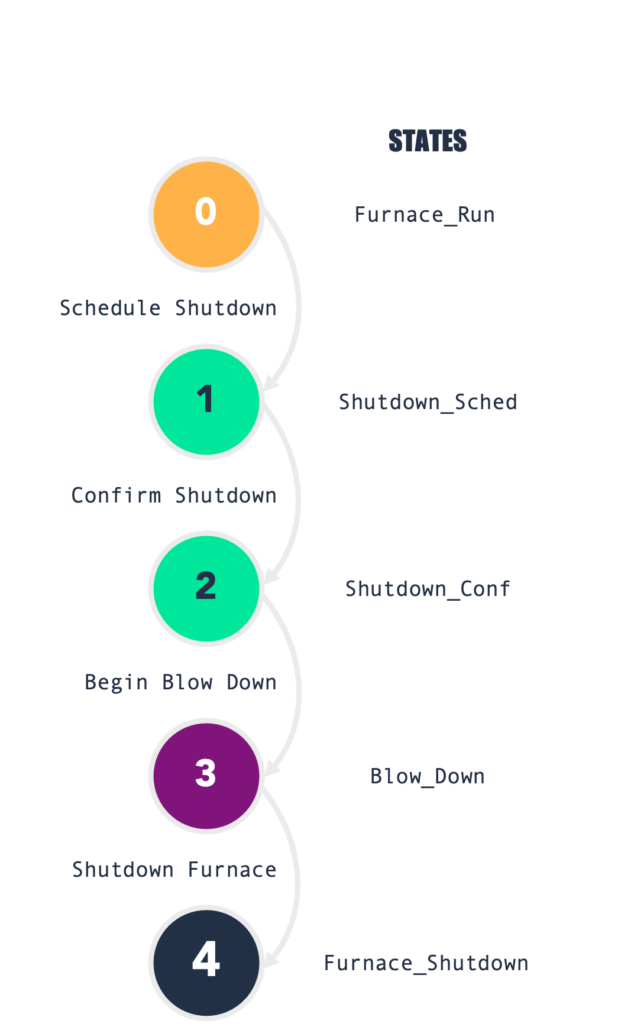
Since a blast furnace is rarely shut down the process includes steps to both schedule and confirm a shutdown before it will begin the safe blowdown process for slowly and gradually running down the furnace, without recharging, before it can be considered safely shut down.
If an attacker is looking to cause serious damage, as they were with the German Steel Mill attack in 2014, their goal would be to skip over the safe shutdown procedures, including the crucial blowdown process, and send the furnace straight to the shutdown state. This can have extremely dangerous consequences, like the buildup of gas in the blower system which can lead to an explosion and potential loss of life.
This type of attack can be prevented with a CoreGuard Finite State Machine micropolicy, which is an example of a safety policy that ensures the safe and proper functioning of a critical finite state machine system.
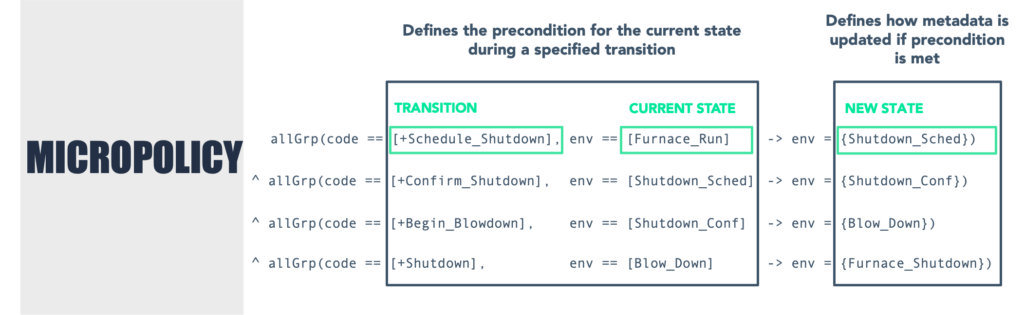
CoreGuard’s finite state machine micropolicy defines the safe states of a system and enforces only the allowed transitions from one safe state to the next. As a result, CoreGuard can stop attacks that attempt to circumvent the safety protocols of a finite state machine, which in an industrial environment can result in danger to life and catastrophic physical damage.
CoreGuard can protect finite state machines with a simple rule, shown above, that essentially cross-checks each transition (or instruction) against the current state of the finite state machine. If the instruction is trying to jump to an out-of-order transition, like straight from running normally to shutdown, CoreGuard will stop it from executing and issue a violation.
With embedded systems in smart factories controlling heavy-duty equipment. providing the highest level of safety and security in those systems needs to be a top priority. When cyberattacks like the German Steel Mill Attack target these systems, there is a serious risk to human safety that needs to be addressed.
To learn more about how CoreGuard can protect safety-critical systems, read our white paper Safety in our Embedded Systems.
Download NowOur Solutions
Finite State Machine
Function: Define the safe states of a system and enforce only the allowed transitions from one safe state to the next.
Type of Attacks: Stops attacks that attempt to circumvent the safety protocols of a finite state machine.


